How-to Handle Suspected Malware in ABB Software
This guide describes how to determine if a malware suspicion is correct or false and how to handle both scenarios. It also includes information about how malware is detected in ABB software.
Intended for
Product owners, L4 coordinators, L4 engineers, software engineers, and L3 Support.
Activities
This flowchart gives an overview of how to handle suspected malware in ABB software.
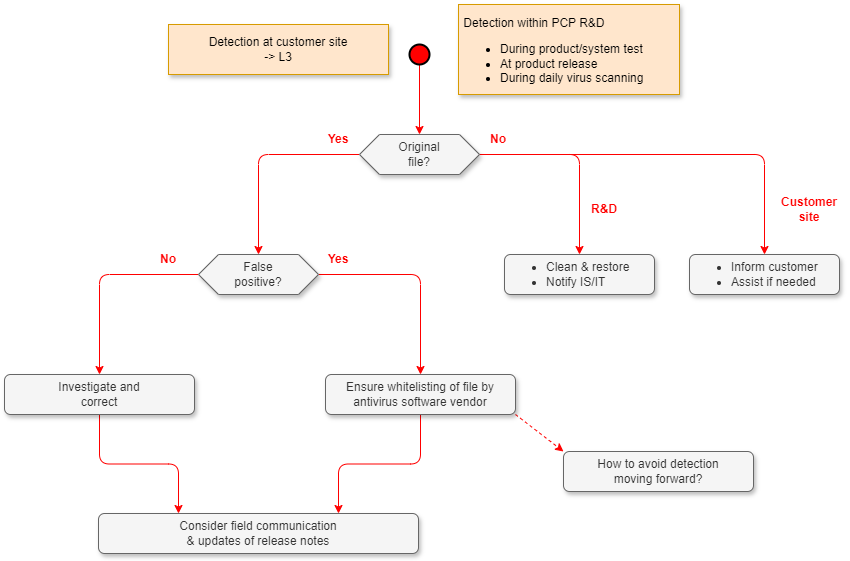
The actions to be taken when a suspected malware has been detected depends on where the detection takes place:
- Within PCP R&D during product development (e.g. in product or system test, release scanning, or daily virus scanning).
- Outside of PCP R&D.
Actions when detected within PCP R&D
Investigate if the detection is on the original file as described in the section Check if the file has been changed.
- If the detection is on the original file: Contact the product responsible team. The product team needs to investigate if the detection is correct or not as described in Investigate if a detection is false or true below, and to determine how to avoid this detection in the future.
- If the file was not the original file: Clean and restore/reimage the computer and notify local IS/IT that malware was detected.
Actions when detected outside of PCP R&D
If malware detection on ABB software happens anywhere outside of R&D, it shall be reported to L3 Support. L3 shall do as follows:
- Guide the customer organization to check if the suspected file is the same as the original file as described in the section Check if the file has been changed below.
- If the detection is on the original file and the detection was done using a supported malware protection solution:
- Request the product responsible team to investigate if the detection is correct or not as described in Investigating if a detection is false or true below, and to determine how to avoid this detection in the future.
- If the detection is false, request the product responsible team they make sure that the file will be whitelisted by the malware protection vendor and get the timeline for this.
- Consider update of release notes if needed, describing it as a known issue.
- Consider field communication if applicable.
- If the detection is on the original file, but the detection was not done using a supported malware protection solution:
- Recommend the customer to change to a supported malware protection solution.
- If the customer does not want to do so: Suggest that the customer contacts the used malware protection vendor and requests that the file is whitelisted.
- If the file was not the original file: Inform the customer organization that the file is not the original file. Assist the customer organization to remediate the issue.
Check if the file has been changed
This flowchart gives an overview of how to check if a file has been changed. The workflow is further explained in the text below.
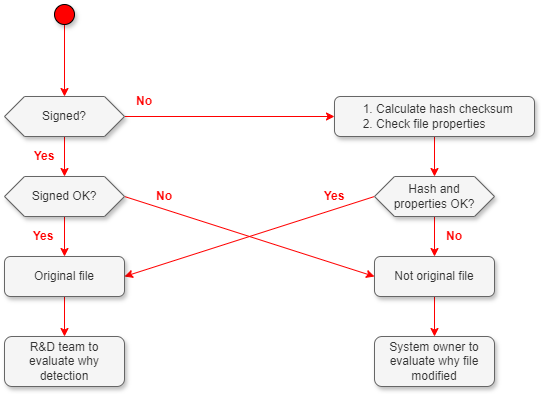
The first thing to check after detection is if the file has been changed since it was created by ABB.
To check if a file has been changed after it was created by ABB, first check if the file is signed and if the signature is ok. This is described in Files with digital signatures below. If the file is not signed, the file properties including a hash checksum should be checked. Contact the product responsible team to get the file properties including the hash checksum. This is described in the Unsigned files below.
If the suspected file matches the original file, the product responsible team should be asked if they are certain that the original file does not contain malware (e.g. if a malware protection company already analyzed the file).
If they are certain that the original file does not contain malware the detection is a false positive.
The section Investigate if a detection is false or true below describes how to conclude if the original file contains malware or not. This work shall be led by the product-responsible team.
Files with digital signatures
The easiest method for checking if a file has been changed after it was created by ABB is to check if the file is signed (irrespective of internal or release signed). If it is a signed file Windows can check if the signature is OK, see steps below. If the signature is OK, the file has not been changed after it was signed. ABB software should be signed by ABB.
Note:
- ABB signs most delivered files of file types that can be signed.
- ABB does not sign files from 3rd party vendors.
- Most ABB-signed files should have the following signing information:
- Name: ABB Asea Brown Boveri Ltd.
- E-mail: seapr-devsupport.seapr@se.abb.com
- Some older signing certificates have also been used. One example is:
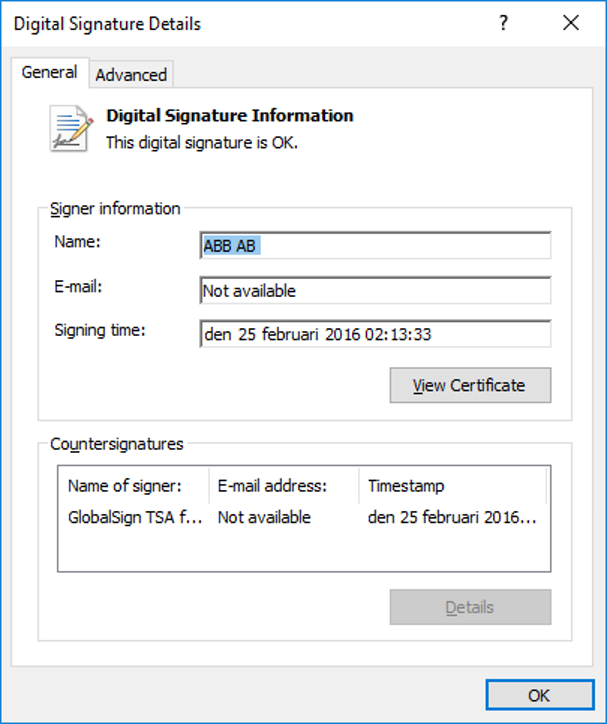
- Name: ABB AB
- E-mail: Not available
Use Windows to check the digital signature of a file. If Windows states that “This digital signature is OK” you can be reasonably sure that the file has not been changed since it was signed.
-
Right-click on the file and select “Properties”.
Signed files have a tab called “Digital Signatures”. Unsigned files do not have this tab.
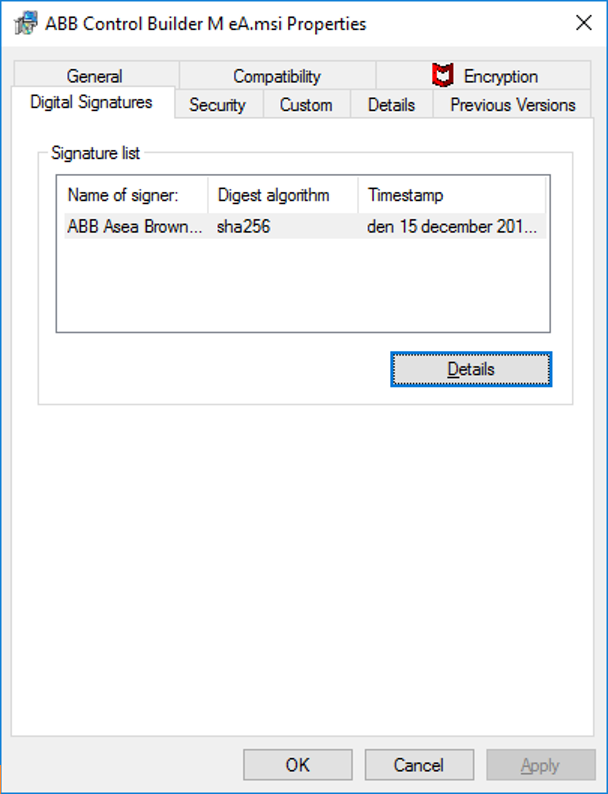
-
Click on “Details” to see the "Digital Signature Information" where it should be stated “This digital signature is OK” if the file has not been changed since it was signed.
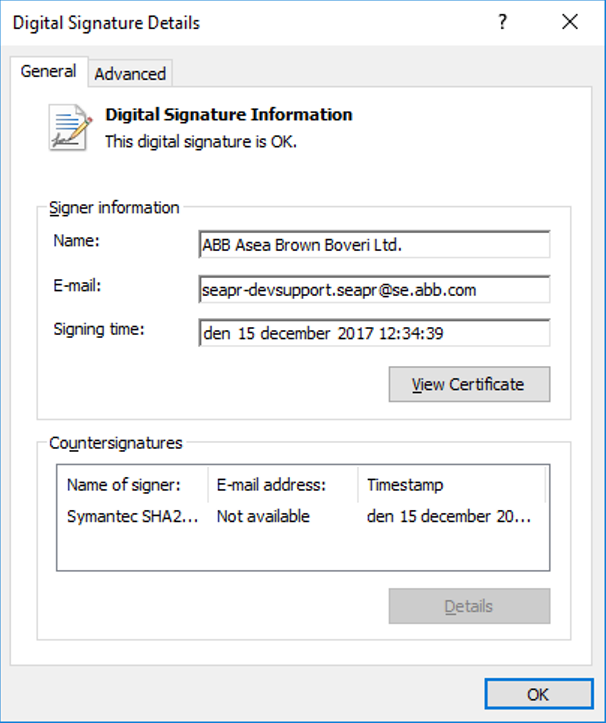
This is another example of how it can look:
Unsigned files
To detect if an unsigned file has been changed the following file properties should be checked:
- File name.
- File date.
- File size.
- Hash checksum.
The hash checksum should be calculated with one of these algorithms:
- Recommended: SHA-256.
- Acceptable: SHA-1 (considered broken, but can give a good hint).
- Last resort: MD5 (considered very broken).
Certutil, a built-in command-line tool that works in both Windows CMD and PowerShell, can be used to calculate the hash checksum of a file. Follow the below instructions for the different algorithms:
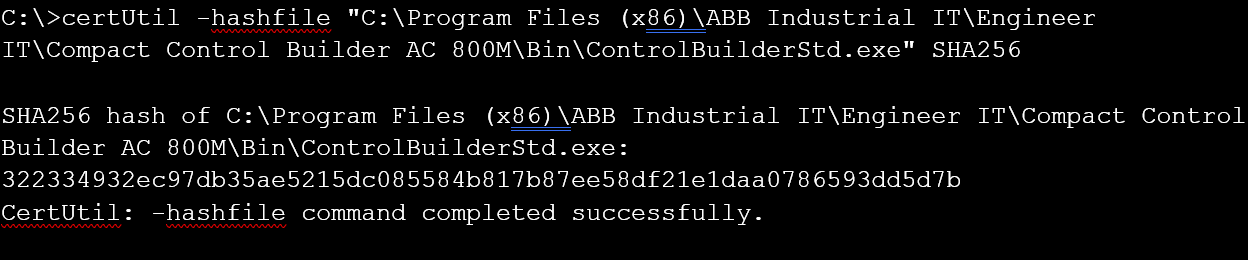
- To calculate the SHA-256 hash checksum of a single file, run the following command in the Windows CMD:
C:\> certUtil -hashfile “C:\file.img” SHA256
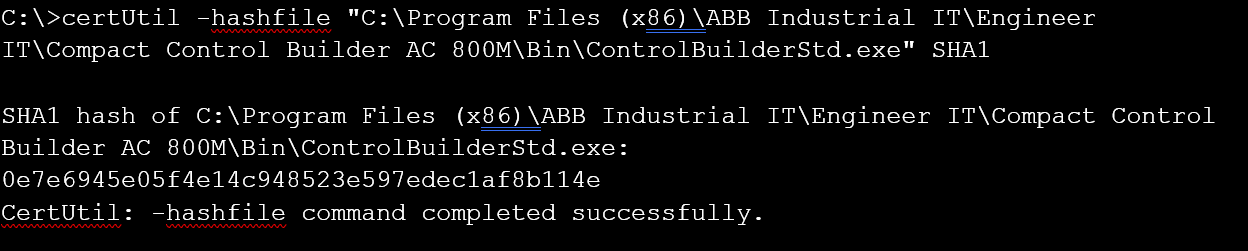
- To calculate the SHA-1 hash checksum of a single file, run the following command in the Windows CMD:
C:\> certUtil -hashfile “C:\file.img” SHA1
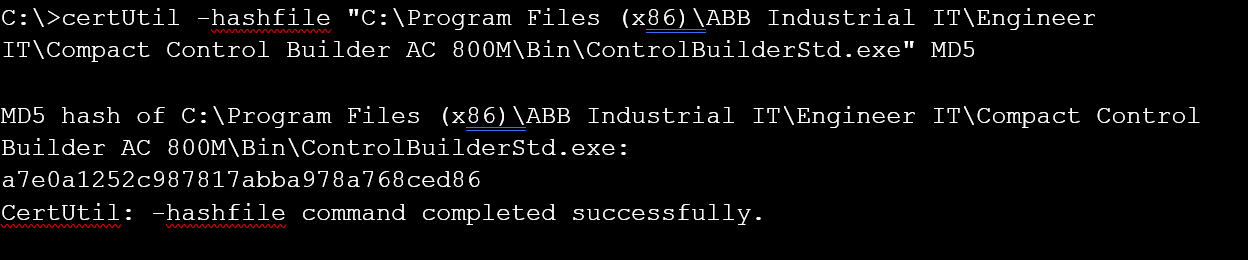
- To calculate the MD5 hash checksum of a single file, run the following command in the windows CMD:
C:\> certUtil -hashfile “C:\file.img” MD5
Investigate if a detection is false or true
Note: The first time a file is flagged with malware it may be difficult to know for certain if the detection is correct or not, even for the developers. How does one know that the build toolchain has not been compromised? And if the file was built long ago: What does one know about the tools and how they were used?
When malware detection software indicates that ABB software contains malware, the following steps should be followed:
-
If the detection is done by supported malware detection software, the vendor(s) of the software should be contacted and requested to investigate the file. If they agree that the file is clean, they should include the signature of the file in an update of the malware definition files for their scanners. The product team responsible for the file can either contact the vendor(s) themselves or get help from the 3rd-party software manager.
-
If the detection is done by malware detection software other than Trellix, Symantec, or Microsoft, we can assume that the detection is a false positive. The product team may still decide to report a false positive detection to the antivirus vendor if they think that there is a risk of getting additional detections in the future and if they want to be nice to the organization that reported the problem.
-
In addition to concluding if the detection is correct or not the product responsible team should consider if the design needs to be changed. This is described in Actions when a clean file is detected as malware below.
Contact supported malware protection vendors
Contact Trellix
- PAPCP products shall be scanned using Trellix Endpoint Security and most products support installing Trellix Endpoint Security on the same computer.
- False positives found by Trellix Endpoint Security Virus Scan shall be reported to Trellix. Concerned teams/users can reach out to 3rd Party Software manager to raise a ticket with Trellix.
- The concerned product team along with 3rd Party Software manager will then work with Trellix to whitelist the files such that the false positives are addressed as soon as possible.
- Once Trellix corrects the issue it will release a new Extra DAT file or new DAT file which will carry the signature of the file.
Contact Symantec
- PAPCP products shall be scanned using Symantec Endpoint Protection and many products support installing Symantec Endpoint Protection on the same computer. False positives found by Symantec Endpoint Protection shall be reported to Symantec.
- Concerned teams/users can reach out to 3rd Party Software manager to raise a ticket with Symantec.
- The concerned product team along with 3rd Party Software manager will then work with Symantec to whitelist the files such that the false positives are addressed as soon as possible.
- Once Symantec corrects the issue it will release a new definition file which will carry the signature of the file.
Contact Microsoft
- PAPCP products shall be scanned using Windows Defender. False positives found by Windows Defender shall be reported to Microsoft.
- Concerned teams/users can reach out to 3rd Party Software manager to raise a ticket with Microsoft.
- The concerned product team along with 3rd Party Software manager will then work with Microsoft to whitelist the files such that the false positives are addressed as soon as possible.
- Once Microsoft corrects the issue it will release a new definition file which will carry the signature of the file.
Contact MetaDefender
- PAPCP products shall be scanned using MetaDefender. False positives found by MetaDefender shall be reported by submitting a ticket.
- A ticket can be submitted using this link.
Actions when a clean file is detected as malware
As described in Investigate if a detection is false or true, a way to avoid false positive detections is to report the file to malware protection vendors, but the product responsible team should not stop after this.
Malware detection on an original file from the product team normally means that something is strange with the file. In most cases, it means that the design in some way does not follow standard design practices. It might do something that malware typically does. It could be that it implements some security-related function in a strange way.
Some examples that have caused malware detections:
- Software that accesses data, files, or registry items that normal applications do not access.
- Software that installs takes over login functionality from Windows.
- Software that encrypts itself.
- Software, other than installation packets, that copy files to program files folders.
A file that has been indicated to contain malware shall be reviewed to see if it would be possible to change the design to follow accepted good design practices.
The risk for false positive malware detection is lower on a properly signed file, so a short-term solution while planning for a later redesign is to sign the file if it was not signed before.
Details
How malware is detected in ABB software
ABB software, that previously has not been flagged to contain malware, can at a new malware detection scan be indicated as malware. Some of the more likely reasons are:
- The software has been altered by malware.
- The malware scanner has been updated with new malware patterns or search capabilities.
- The software has been updated or modified by ABB.
In case 1 the detection is true.
In case 2 it is more likely that the detection is false, but there is also a risk that the ABB Software had contained malware since before but that it had not been detected before.
In case 3 the detection may be either true because the new build was infected during the build process or that the detection is false because the new build matched an existing malware pattern, which the old build did not match. The detection can also be false because the old version was whitelisted by the malware scanner, but the new version is not.
Malware in ABB software can be detected by anyone with malware detection software. ABB wants to find real or false positive detections before its customers and to achieve this several activities are performed:
-
During product and system type testing antivirus software is used to reduce the risk of malware detection in new releases (case 3 above).
-
During product and system type testing, antivirus software from Trellix and Symantec is validated to be compatible with the ABB products. This validation intends to check that:
- The malware detection software does not affect the operation of the ABB product.
- New ABB software is not detected as malware by the supported malware detection software.
-
At product release, all ABB software is scanned by at least three antivirus software. This is the last check before the release and is therefore the most important check to handle case 1 above.
-
ABB performs daily virus scanning with multiple antivirus software to discover if an updated version of any of the antivirus software detects ABB Software as malware (case 2 above).
Malware detection software within ABB
The most commonly used malware detection software within ABB is the following:
- Trellix Endpoint Security.
- Symantec Endpoint Protection.
- MetaDefender Core.
- CylancePROTECT.
- Windows Defender.