How-to Perform Binary Composition Analysis with BDBA
Binary composition analysis is a method used to examine the components inside binary files to detect and manage security risks. This guide describes how to perform such analysis with Black Duck Binary Analysis (BDBA).
It also includes information about BDBA and ABB's policy regarding binary composition analysis.
Intended for
Cyber security engineers, software developers, and 3rd-party software owners.
Prerequisites
- Make sure you have access to the BDBA portal. The software composition analysis (SCA) team is responsible for the onboarding of users and can be reached at SCA@in.abb.com.
- Make sure you have the compiled library file/folder (in a compressed format having multiple files) which is required to be scanned.
- Once you get the login details, log-in to the BDBA portal.
Activities
Scan file
-
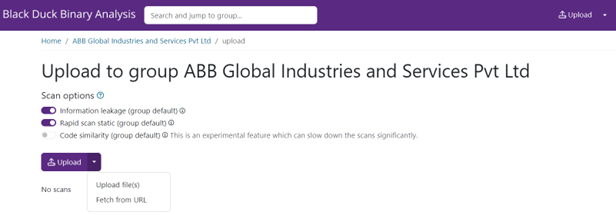
Click on ‘Upload’ and select the appropriate options to add the file to start the scanning of the file.
-
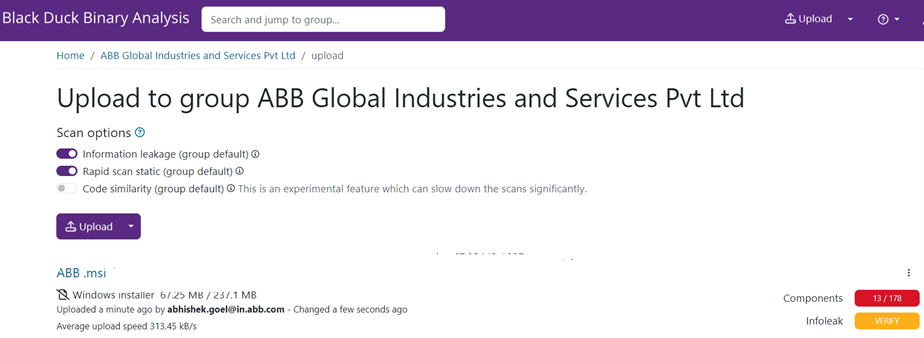
Once the upload finishes, a scan starts automatically and shows the basic details upfront.
-
Select the file name, i.e. “ABB.msi”, in the above screenshot. A detailed view will be presented.
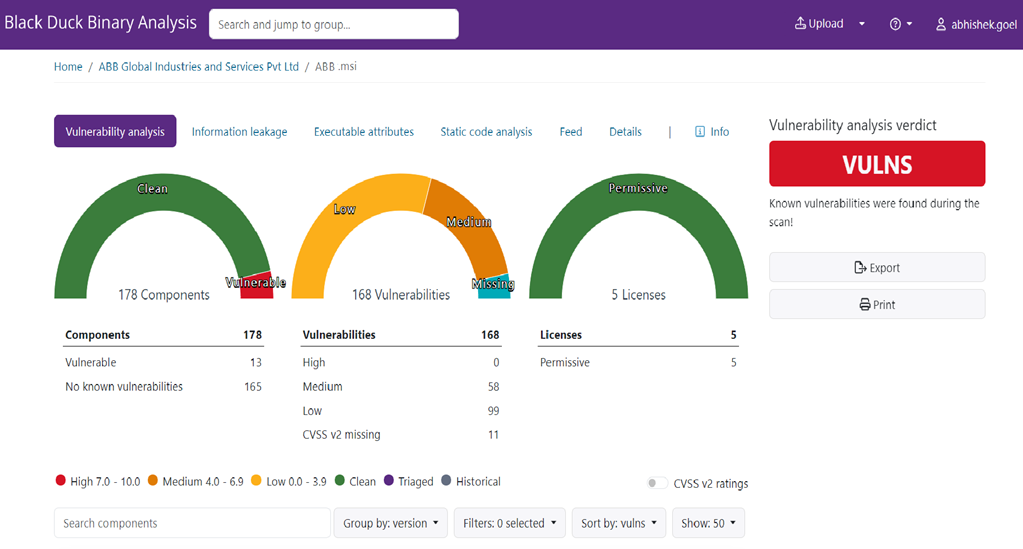
In the top-right part of the page, you can see the vulnerability analysis verdict as shown in the below snapshot. This is the overall verdict of your scan and can be one of the following:
-
PASS: No known vulnerabilities were found during the scan.
-
VULNS: Known vulnerabilities were found during the scan.
-
N/A: No components or licenses could be identified.
-
VERIFY: Possible vulnerabilities were found during the scan.
-
Evaluate results
The team must analyze the scanning result under each of the tabs:

-
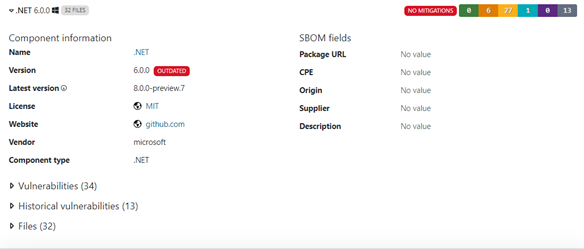
The "Vulnerability Analysis" tab shows the vulnerability information for the components being used inside the library, here shown for
.Net6.0.0.as an example.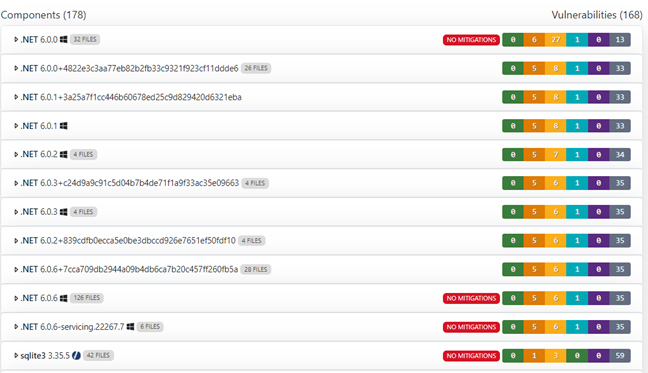
-
The "Information Leakage" tab displays unintentional leakage of possibly sensitive data that is contained within a software package.
-
The "Executable Attributes" tab displays the executable attributes found in the analysis, their severities, and attribute types. Executable attributes indicate missing exploit protection in code, making exploitation of possible vulnerabilities easier.
-
The "Static code analysis" tab gives the results of the source code analysis.
Create bugs
Create bugs for all issues identified under the tabs above. The bugs should then follow the bug lifecycle process described in How-to Manage Bugs.
Details
ABB's policy regarding binary software composition analysis
All ABB products or system offerings should perform binary software composition analysis. In PAPCP we currently recommend using BDBA for the binary analysis with the following goals (as required by IEC 62443-4-1 SVV-3d):
The analysis should be performed:
- For compiled software.
- On all binary executable files, including embedded firmware, delivered by the supplier to be installed for a product.
The analysis shall detect the following types of problems at a minimum:
- Known vulnerabilities in the product software components.
- Linking to vulnerable libraries.
- Security rule violations.
- Compiler settings that can lead to vulnerabilities.
What is BDBA and why is it needed?
Security aspects of all ABB software shall be analyzed. Source code is scanned with Black Duck Hub to identify open source components that are analyzed for risks related to license obligations, obsolescence and vulnerabilities. BDBA is used to scan binary code. It analyzes security aspects of both 3rd party binaries (both commercial and open source components) and binaries developed inhouse by ABB.
Binary analysis is a type of code review that looks at files composed of binary code and assesses their content and structure, all without the need for access to source code.
Binary analysis helps teams to inspect binary code, and to identify open-source components, security vulnerabilities, license obligations not required, and additional sensitive information that could lead to a breach.
BDBA identifies open-source components in compiled software to provide a list of any vulnerabilities and licenses related to those components.
BDBA also recognizes compiler switches, mobile permissions, and other forms of information leakage that could potentially expose sensitive information. Furthermore, BDBA goes beyond simply detecting these issues; hand-crafted security advisories (Black Duck Security Advisory i.e. BDSA) provide detailed notifications for each vulnerability identified, giving users the information needed to properly understand, prioritize, and remediate the problem.
BDBA will help teams to find the vulnerabilities in their applications without access to source code. Since static testing solutions based on binary analysis rely on modeled datatypes, data, and control paths, manual inspection of the findings can help improve the efficacy of such binary analysis. This helps eliminate noise and false positives during the assessment, making it easier to discover vulnerabilities and get actionable remediation guidance.